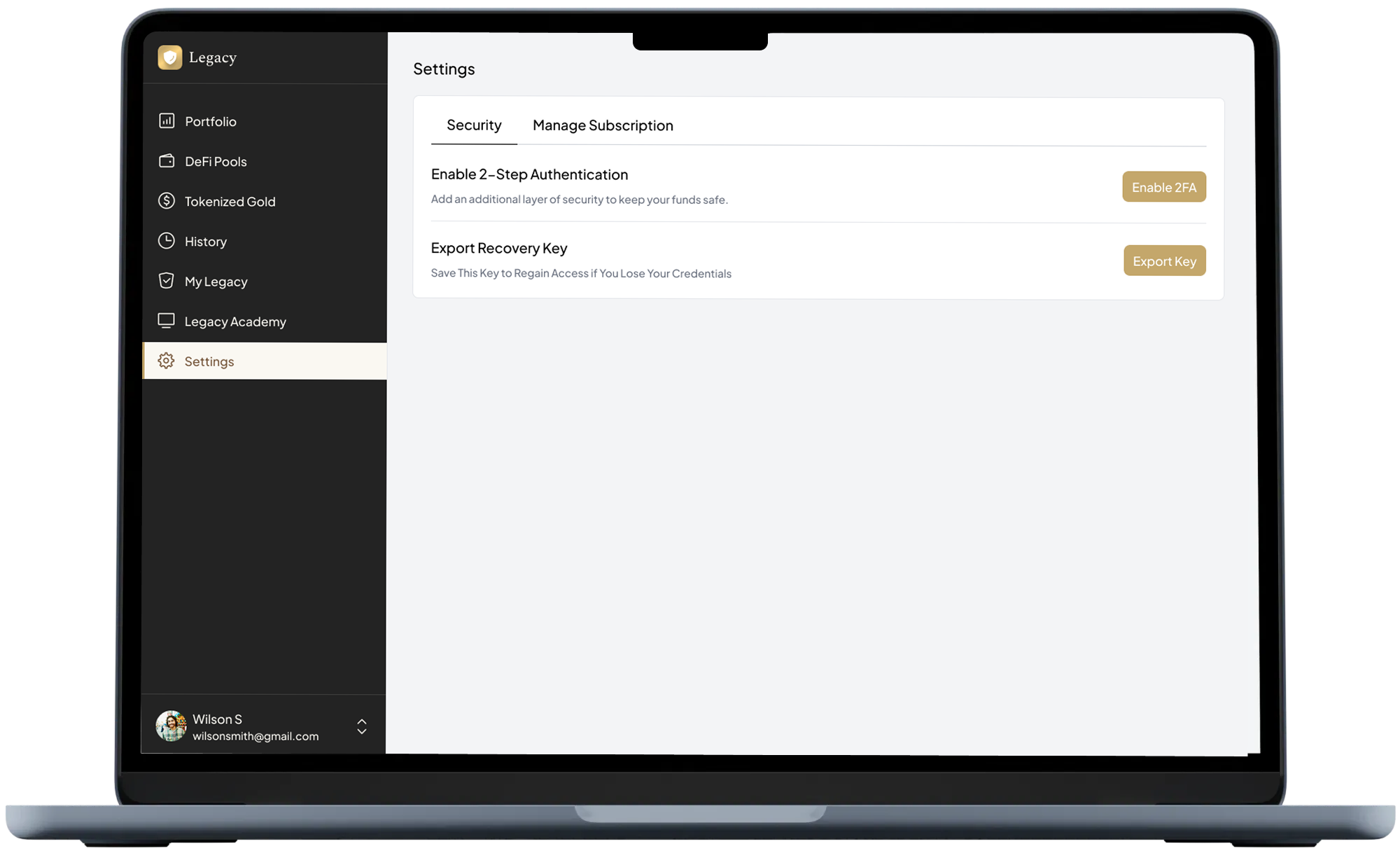
Security isn’t just infrastructure, it’s also how you access Legacy.
- 2FA for account login
- Email confirmations for sensitive actions (where applicable)
- Session monitoring & alerts for unusual activity
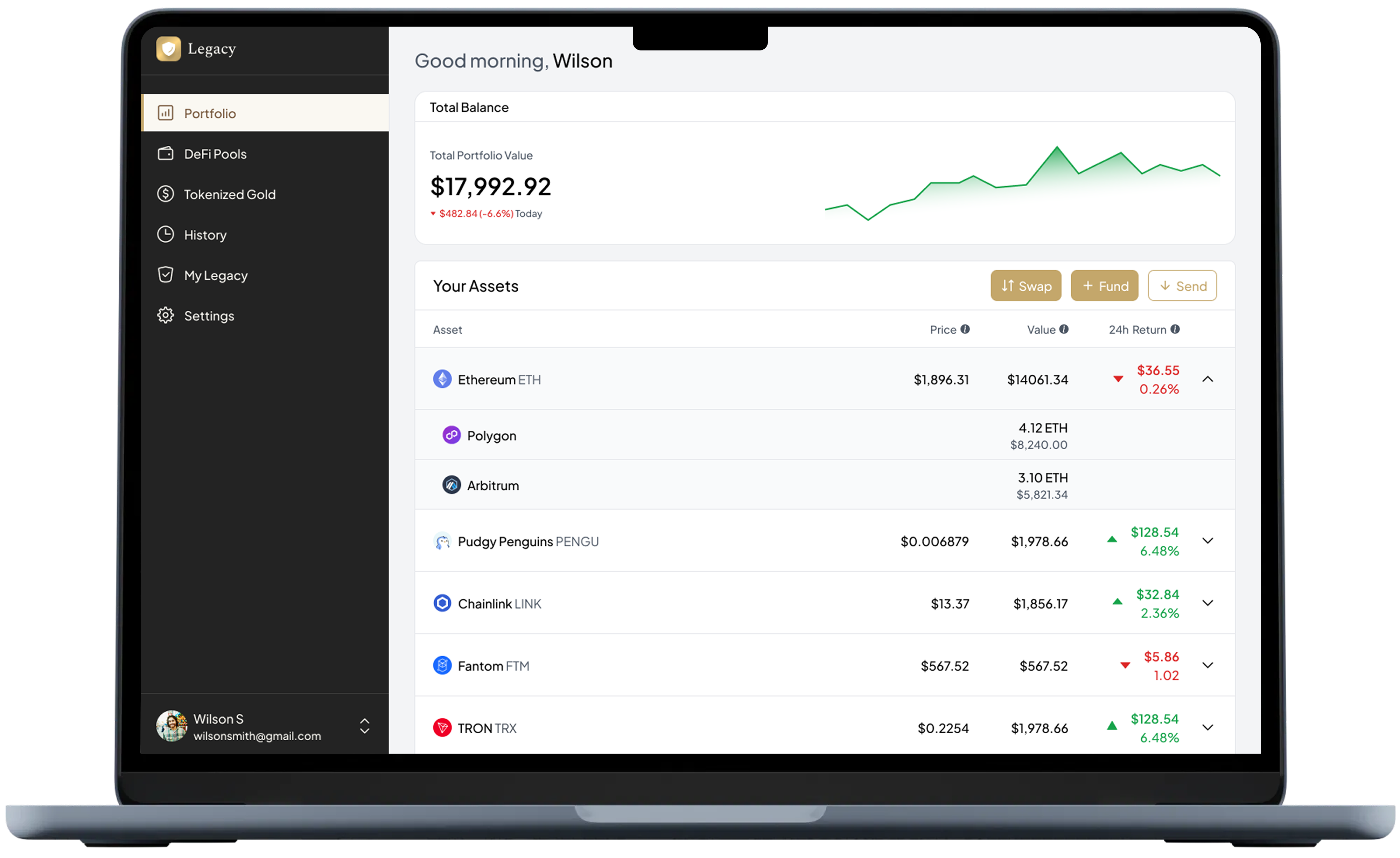
- Unified dashboard across all chains, giving you complete visibility without shifting assets.
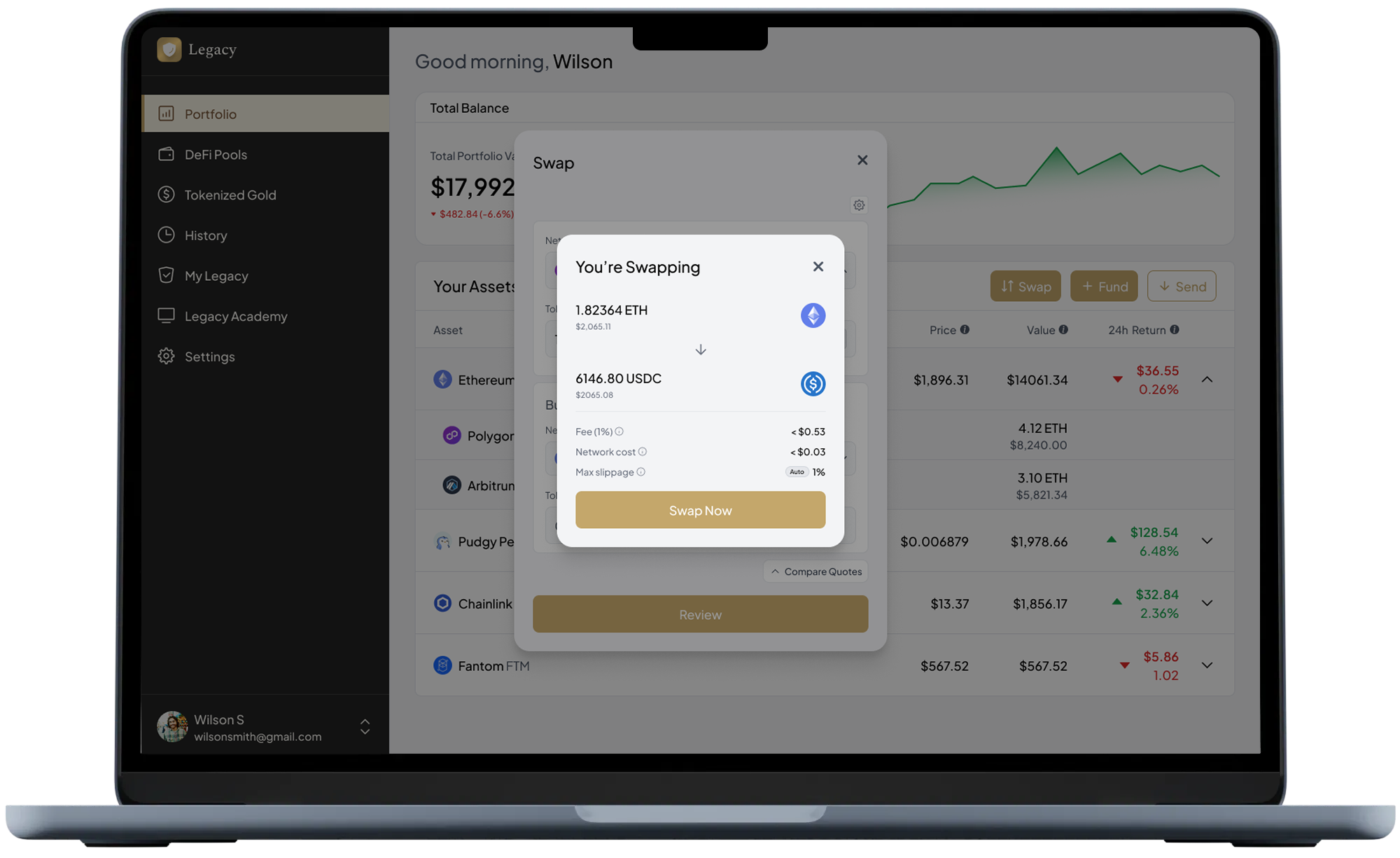
- Transparent fee model: before any swap or transaction you see network fees + Legacy fee.
- Security-first design: built for everyone from beginners who protect their first $10k to investors protecting serious portfolios.
Our VIP Support Line is available for subscribers to help you if you suspect anything unusual.